
PerfektBlue is the industry-wide critical over-the-air attack chain affecting millions of devices in automotive and other industries. The exploitation chain covers multiple vulnerabilities found in the specific Bluetooth stack highly utilized in the industry. Successful exploitation of the identified vulnerabilities leads to Remote Code Execution on a target device.
Bluetooth. BlueSDK
Bluetooth is a technology standard that is used for exchanging over-the-air data between devices over short distances, usually within 10 meters. As long as Bluetooth is only a standard, there are a lot of implementations of this technology such as Fluoride in Android, bluez in Linux, and others.
OpenSynergy's BlueSDK is one of Bluetooth implementations that is widely used in the automotive industry specifically. This stack is hardware-agnostic, supports both BR/EDR (Classic) and Low Energy operations, implements a lot of standard Bluetooth profiles, and has a closed-source implementation.
BlueSDK is considered as a Bluetooth framework which means that vendors might change parts of the implementation or configurations to tune it for their systems.
PerfektBlue.
1-click RCE attack
PerfektBlue exploitation attack is a set of critical memory corruption and logical vulnerabilities found in OpenSynergy BlueSDK Bluetooth stack that can be chained together to obtain Remote Code Execution (RCE) on millions of transport vehicles manufactured by completely different and unrelated vendors. As BlueSDK is a Bluetooth framework that can be used not only in automotive, other industries might be affected as well.
The only requirement for PerfektBlue attack is the pairing with the target device to have an appropriate security communication level. However, this limitation is implementation-specific due to the framework nature of BlueSDK. Thus, pairing process might look different between various devices: limited/unlimited number of pairing requests, presence/absence of user interaction, or pairing might be disabled completely.
Essentially, PerfektBlue requires at most 1-click from a user to be exploited over-the-air by an attacker.

Affected Devices. Impact
Turned out that OpenSynergy BlueSDK framework is widely used in automotive industry in particular. BlueSDK is used in other domains as well (for example, in mobile phones and portable devices) but most of the potentially vulnerable devices are automotive-related.
Public resources containing Bluetooth certification information were used to identify vendors and products using BlueSDK framework. The following is a non-extensive list of affected vendors: Mercedes-Benz AG, Volkswagen, Skoda
Having code execution on IVI device, it's possible for an attacker to track GPS coordinates, record audio inside a car, obtain personal phonebook information, and finally perform lateral movement to other ECUs - legitimately or by exploiting other software components - and obtain access to critical elements of a car.
To protect against PerfektBlue, you can update your system or disable the Bluetooth functionality entirely.
Demo
We demonstrate the criticality of PerfektBlue attack with proof-of-concept exploits for three Infotainment systems of different vendors. You can refer to the Advisory for more detailed information about these devices.
It's important to note that each demonstrated device is one of many vulnerable infotainment systems for each vendor (like NTG6 and NTG7 in Mercedes-Benz). We have means to think that lower and upper (2024-2025) firmware versions for each device and vehicle model line are likely to be exploitable as well.
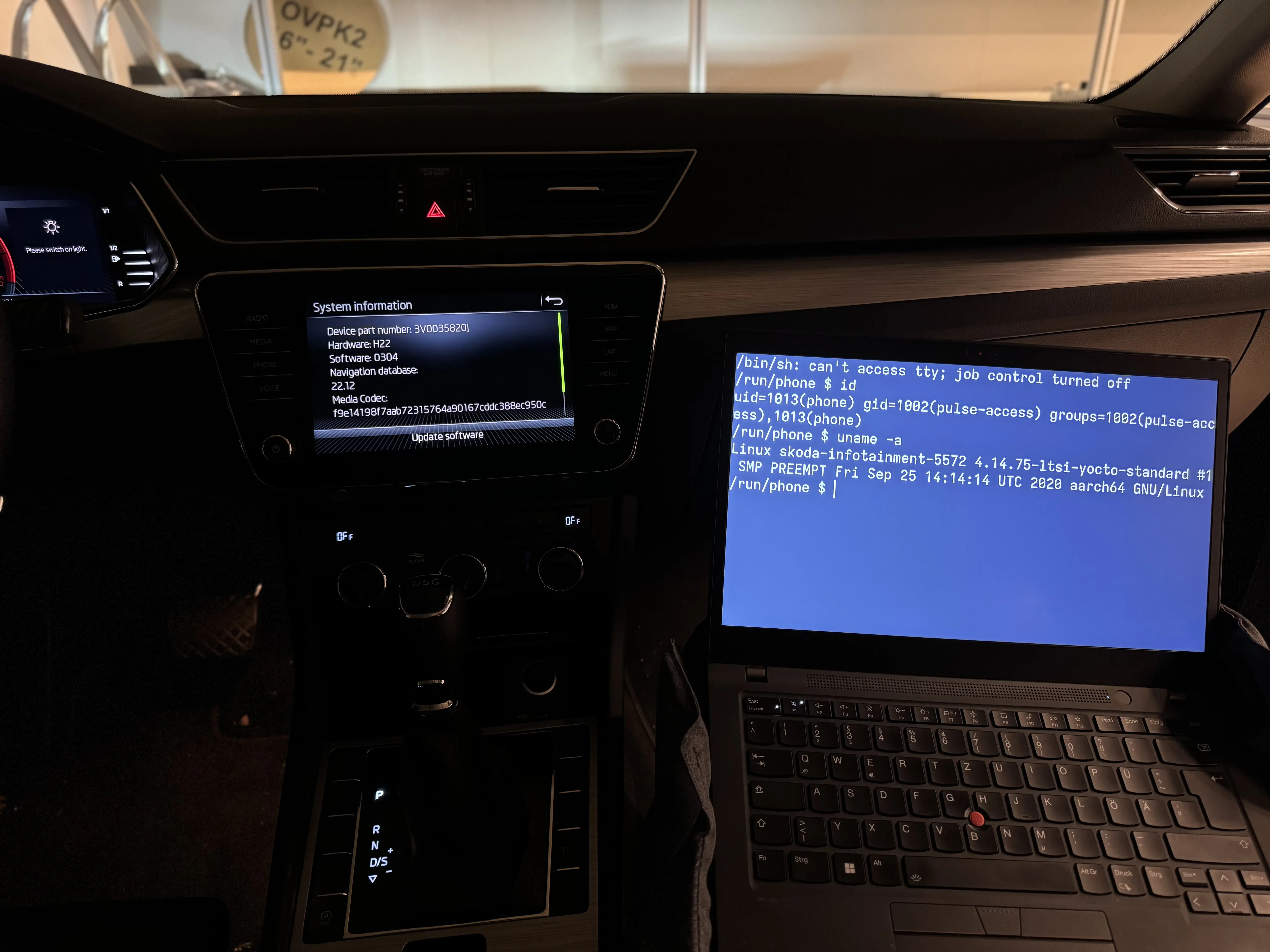
Volkswagen ID.4
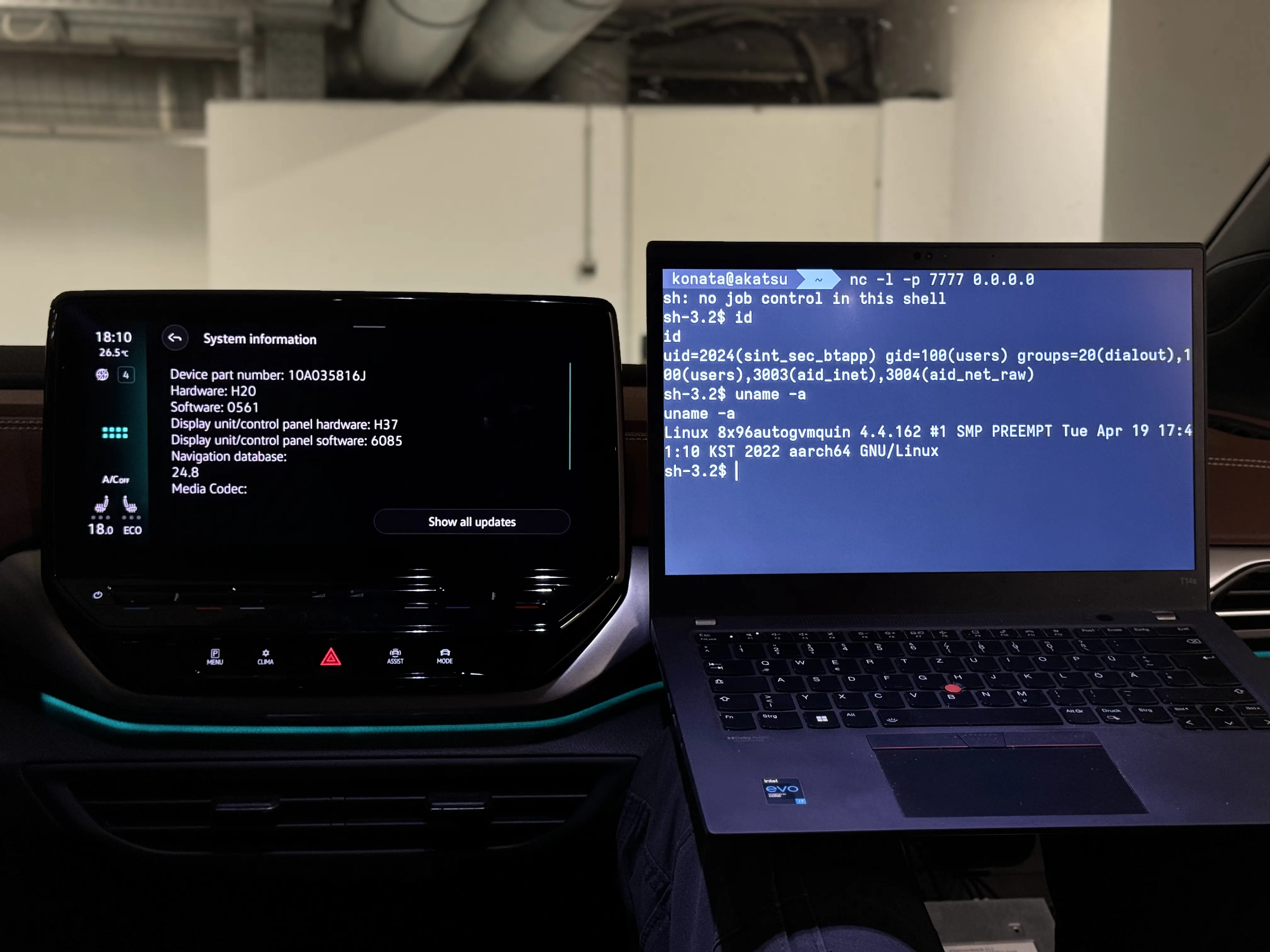
In the first demo, we use Volkswagen MEB ICAS3 infotainment system for exploit verification. The mentioned device is installed on Volkswagen ID model line. The exploit verification was conducted for 0561 and 0792 firmware versions.
On the right is the demonstration of the reverse shell obtained on top of TCP/IP after successful PerfektBlue exploitation (on 0561 firmware version). As you can see, an attacker gains sint_sec_btapp user permissions within the IVI system.
Mercedes-Benz
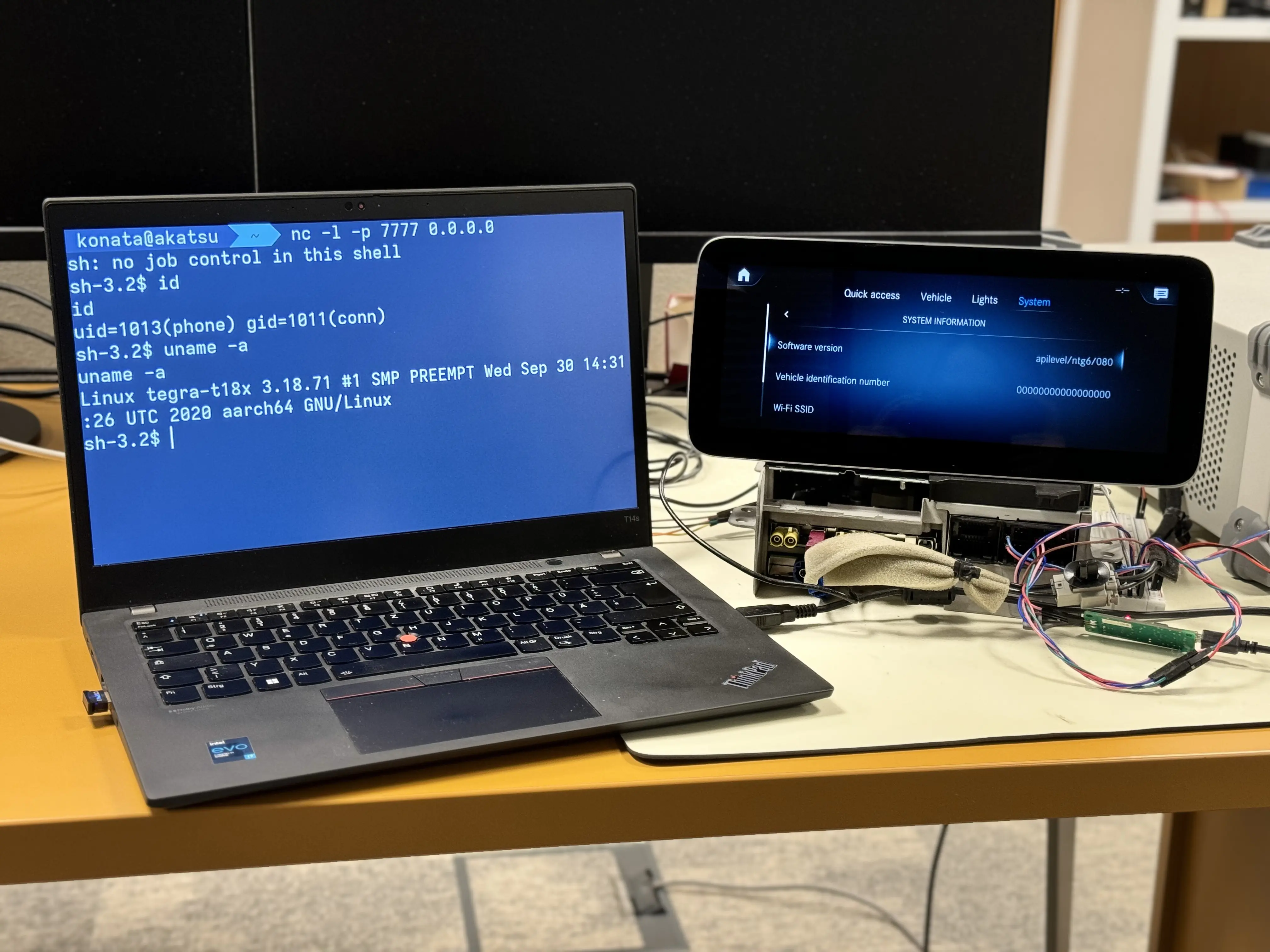
The second proof-of-concept exploit shows how PerfektBlue can be used to obtain RCE on Mercedes-Benz NTG6 head unit. The latest-generation head unit model, NTG7, (2024-2025) may also be affected, as it is mentioned in the list of devices using BlueSDK.
On the left is the demonstration of the reverse shell obtained on top of TCP/IP after successful PerfektBlue exploitation. An attacker gains phone user permissions.
Skoda Superb
The third demonstration covers Skoda MIB3 head unit as a potential target for PerfektBlue attack. The mentioned head unit is installed on Skoda Superb model line and some Volkswagen model lines.
On the right is the demonstration of the reverse shell obtained on top of TCP/IP after successful PerfektBlue exploitation. An attacker gains phone user permissions.
FAQ on PerfektBlue
How severe is PerfektBlue attack?
PerfektBlue allows an attacker to achieve remote code execution on a vulnerable device. Consider it as an entrypoint to the targeted system which is critical. Speaking about vehicles, it's an IVI system. Further lateral movement within a vehicle depends on its architecture and might involve additional vulnerabilities to get access to critical elements of a car (body, engine, etc). For other domains such as mobile phones and portable devices, it also depends on their internal system architecture.
Which devices are at risk?
Any product having its Bluetooth stack based on BlueSDK framework is potentially vulnerable. Based on our research, this applies mostly to automotive domain.
Is OpenSynergy aware of this attack?
Yes, we reported all the findings to OpenSynergy in May, 2024. They acknowledged, and rolled out patches to the customers of BlueSDK in September, 2024. It was decided to wait until all of OpenSynergy customers applied the patches before this publication
Am I affected by PerfektBlue?
We don't know for sure. It depends on various factors such as what Bluetooth stack is used on your device, its firmware version, etc. We recommend contacting your vendor for more information regarding PerfektBlue.
Where can I read about the actual vulnerabilities used in PerfektBlue?
All the technical information regarding vulnerabilities, CVE numbers, and exploitation can be found in our Slides (will be published later) or Advisory pages.
How do I know if my device is based on OpenSynergy BlueSDK framework?
Until you have the firmware of your device, it's hard to tell. There are public resources that might contain some intel about it, such as websites with Bluetooth certification information.
What should I do to patch vulnerabilities of PerfektBlue?
Download the latest software update for your device ASAP if you're the owner of an affected product listed in Affected Devices section. Contact the manufacturer of your device/vehicle to confirm that the version of software installed on your product is not affected.
How can manufacturers mitigate the risk?
If you're a manufacturer and aren't sure if your products are affected by PerfektBlue, you can contact PCA Team for guidance on verifying and mitigating the vulnerabilities. See PCA contact information at the bottom of this page.
Acknowledgements
Mikhail Evdokimov is the original author of PerfektBlue.
However, this research wouldn't be possible without help and contribution of the whole PCA Security Assessment team:
• Abdellah Benotsmane
• Aleksei Stennikov
• Artem Ivachev
• Danila Parnishchev
• Polina Smirnova
• Radu Motspan
